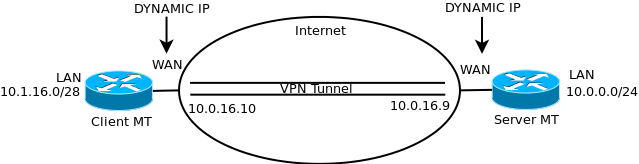
Server side
On the server side we first create an user who will connect to the server: (Be sure to set a complex password and a longer username)/ppp secret add caller-id="" comment="Some description" disabled=no limit-bytes-in=0 \ limit-bytes-out=0 local-address=10.0.16.9 name=ka password=ka profile=default \ remote-address=10.0.16.10 routes="" service=l2tpThen we create a L2TP server interface for the created user:
/interface l2tp-server add disabled=no name=l2tp-ka user=kaCreating the server interface is not nececery for all this to work since the ROS will dynamicly create the interface each time the user authenticates, but will ease creation of firewall rules.
Enable the server:
/interface l2tp-server server set authentication=pap,chap,mschap1,mschap2 \ default-profile=default-encryption enabled=yes max-mru=1460 max-mtu=1460 mrru=disabledAdd a route to the client side network:
/ip route add comment=Ka disabled=no distance=1 dst-address=10.1.16.0/28 gateway=10.0.16.10 \ scope=30 target-scope=10Don't forget to change the dst-address to your IP range on the client side
Here is where you have to take a break from this script and read this script. Since you don't have any static IP addresses, you will need a dynamic DNS on the serve side. Once you have configured the ChangeIP.org script from the link, proceed to the client side configuration.
Client side
Create a l2tp client interface to connect to the server. Change IP_OF_L2TP_SERVER to an IP address of your server side router./interface l2tp-client add add-default-route=no allow=pap,chap,mschap1,mschap2 \ connect-to=IP_OF_L2TP_SERVER dial-on-demand=no disabled=no max-mru=1460 \ max-mtu=1460 mrru=disabled name=l2tp-BL password=ka profile=default-encryption user=kaAdd a route to the server side network:
/ip route add disabled=no distance=1 dst-address=10.0.0.0/24 gateway=10.0.16.9 scope=30 \ target-scope=10Don't forget to change the dst-address to your IP range on the server side
Now to make the link work after one of the IP addresses change.
First add a script named 'SetL2TP' and with the following code:
:global newr1 [:resolve hostname.changeip.org] /int l2tp-client set l2tp-BL connect-to=$newr1 :log info "SetL2TPscript:Changing IP"When executed, this will resolve the new IP to the ChangeIP.org hostname you have set on the server side.
Then add a scheduler that will execute the above script every 60 seconds (make sure the schedular is now disabled):
/system scheduler add disabled=yes interval=1m name=SetL2TP on-event="system script run SetL2TP" \ policy=read,write,test start-time=startupExperiment with this interval. You don't want too short an interval because you might get an IP from cache and not be able to reconnect for a longer time.
Now add two scripts that enable and disable the scheduler above. Just paste these two lines on the MT terminal:
/system script add name=EnaSched_1 policy=ftp,reboot,read,write,policy,test,winbox,password,sniff \ source="sys sched ena SetL2TP" /system script add name=DisaSched_1 policy=ftp,reboot,read,write,policy,test,winbox,password,sniff \ source="sys sched disa SetL2TP"Finally, create a netwatch that checks if server side is avaliable:
/tool netwatch add disabled=no down-script=EnaSched_1 host=10.0.16.9 interval=15s timeout=1s \ up-script=DisaSched_1Netwatch pings the specified IP address (remote end of VPN link in this case) and then executes different scripts if ping was successful or unsuccessful.
How this works
When any side (client or server) changes their IP address and the VPN link fails, netwatch will run the script EnaSched_1 which will enable the scheduler SetL2TP. The scheduler will then try to resolve the ChangeIP.org hostname of the server side and change the IP address on the L2TP client interface accordingly. L2TP client interface will now connect to the server and netwatch ping will now be successful so it will run the script DisaSched_1 which will now disable the scheduler.Now if you need IPSEC on this VPN link, look at this article.
Fuente:
https://wiki.mikrotik.com/wiki/VPN_(any_type)_between_2_Mikrotik_routers_and_no_static_IP_addresses
No hay comentarios:
Publicar un comentario